

|
 |
MITRE has released a freeware tool that allows a company to check the configuration of their Internet point-of-presence router. The tool will help companies determine whether their routers are configured to the Help Defeat Denial of Service Attacks guidelines. This configuration of egress filtering reduces the chance that their computers can unwittingly contribute to a distributed denial of service attack.
The tool has two parts; a generator and a receiver. The test generator (or "client") is being provided as C source code and the test receiver (or "server") is a PERL script. Both are currently known to work on LINUX, and the server also works on Solaris.This egress filtering diagnosis tool is provided as a public service subject to the terms of the License Agreement. This tool is merely an aid; security remains the responsibility of the user.
This tool is intended to assist information security specialists in conducting a vulnerability analysis of their network by identifying potential weaknesses in their network configuration; however, the use of this tool can not guarantee adequate information security or that a network has adequate egress filtering. This tool should not be used on an information system without the specific authorization of the person responsible for the information security of that system. This tool is not intended to serve, and should not be considered, as a substitute for qualified information security specialists or an information security program tailored to your information system. You should consult with a qualified information security specialist to properly interpret the results of this vulnerability analysis and before taking any corrective action.
The tool is available to anyone who would like it. If you desire to discuss the tool, there is an e-mail list for egressor developers and users: egressor-list@lists.mitre.org. Send subscription requests to listserv@mitre.org with "subscribe egressor-list youremail@yourorg Your Name" in the body (i.e. "subscribe egressor-list John.Smith@aol.com John Smith").
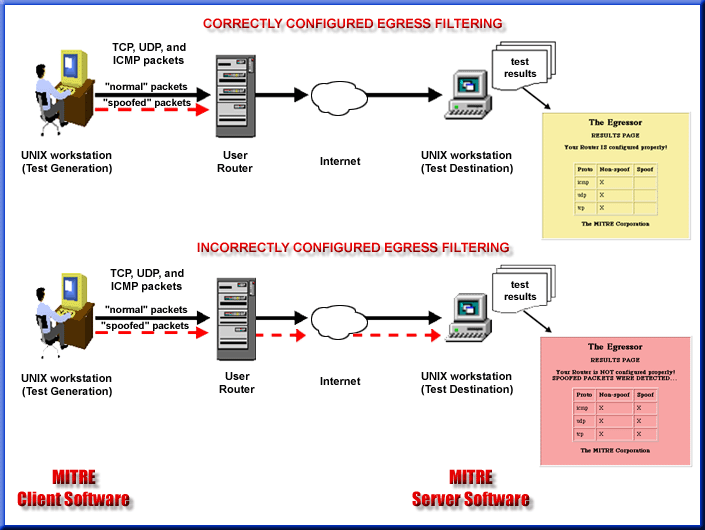
Briefly, the client generates a stream of packets, some of which are spoofed. The server listens for test packets, and determines if spoofed packets were received as part of the test. The server then generates a report of the results, indicating whether spoofed packets were received or not. Figure 1 shows the two scenarios that the tool can find including the html versions of the reports. There is also a "daemon" option which causes the server to run indefinitely.
If you are interested in hosting a server version of the tool on the Internet for general public use, please contact us.
|
|
More Information on Egress Filtering, and Denial of Service Attacks can be found in MITRE's Help Defeat Denial of Service Attacks: Step-by-Step.
Packetfactory home